近年來資安問題頻傳,越來越多裝置(個人電腦,行動裝置等) 透過雲端物聯網(IoT)與雲端儲存相互連結,資料的開放性衍生出許多資安問題和惡意攻擊。除了一般常見的防毒軟體,以軟體層面來防堵之外,硬體層面部分尤其是儲存裝置的防護,會以硬體加密為主,例如常見的「ASE 256bit」加密技術,便是透過儲存裝置內建支援硬體加密的控制器單元,對儲存裝置進行完整磁碟加密。硬體加密的安全性較高,要將資料從硬碟竊取幾乎是不可能的任務。
擁有加密技術的儲存裝置越來越多,但該如何確保其加密功能是真正安全符合規範?TCG組織(Trusted Computing Group)便規劃了「Opal儲存裝置安全規範(Opal Storage Specification)」,符合TCG Opal規範的儲存裝置,可於裝置內執行加密,在效能、安全和管理方面,皆較軟體的加密系統更具資料保密之優勢;也更不影響主機系統作業且不佔用資源,不需要額外的主機加密元件,所有加密皆於裝置內部進行完成。
為了驗證是否符合TCG Opal規範,我們與知名測試驗證工具開發商ULINK Technology合作,利用其開發的測試工具與對應的TCG測試腳本,提供相關TCG Opal Certification Test以及TCG Opal Protocol Test驗證其產品是否能通過測試。我們利用通過TCG組織通過認可的測試工具來對儲存裝置(SATA/NVMe)進行驗證。以下為兩個測試相關介紹。
TCG Opal Certification Test
以可控的識別環境,一致性的判斷標準,可輕易複製問題發生的條件。
為了驗證TCG儲存裝置是否正常符合TCG規範(TCG Storage Architecture Core Specification, Version 2.01; TCG Storage OPAL Family Test Cases Specification, Version 1.00),利用Certification Test針對儲存裝置進行TCG functional check,確認回傳值是否符合spec規範。TCG Opal Certification Test測試項目如下:
| a. Use Case Test Cases: | b. Specific Functionality: | c. Error Test Cases: |
| 1. UCT-01 Level 0 Discovery | 1. SPF-01Transaction | 1. ETC-01 Native Protocol Read/Write Locked Error Responses |
| 2. UCT-02 Properties | 2. SPF-02 IF-RECV Behavior Tests | 2. ETC-02 General IF-SEND /IF-RECV Synchronous Protocol |
| 3. UCT-03 Taking ownership of an SID | 3. SPF-03 TryLimit | 3. ETC-03 Invalid IF-SEND Transfer length |
| 4. UCT-04 Activate Locking SP when in Manufactured Inactive State | 4. SPF-04 Tries Reset | 4. ETC-04 Invalid SessionID – Regular Session |
| 5. UCT-05 Configuring Authorities | 5. SPF-05 Tries Reset on Power Cycle | 5. ETC-05 Unexpected Token Outside of Method – Regular Session |
| 6. UCT-06 Configuring Locking Objects (Locking Ranges) | 6. SPF-06 Next | 6. ETC-06 Unexpected Token in Method Header – Regular Session |
| 7. UCT-07 Unlocking Ranges | 7. SPF-07 Host Session Number (HSN) | 7. ETC-07 Unexpected Token Outside of Method – Control Session |
| 8. UCT-08 Erasing Ranges | 8. SPF-08 RevertSP | 8. ETC-08 Unexpected Token in the Method Parameter List – Control Session |
| 9. UCT-09 Using the DataStore table | 9. SPF-09 Range Alignment Verification | 9. ETC-09 Exceeding Transaction Limit |
| 10. UCT-10 Enable MBR Shadowing | 10. SPF-10 Byte Table Access Granularity | 10. ETC-10 Invalid Invoking ID – Get |
| 11. UCT-11 MBR Done | 11. SPF-11 Stack Reset | 11. ETC-11 Invalid Invoking ID – Non-Get |
| 12. UCT-12 Revert the Locking SP using SID, with Locking SP in Mfg state | 12. SPF-12 TPer Reset | 12. ETC-12 Authorization |
| 13. UCT-13 Revert the Admin SP using SID, with Locking SP in Mfg-Inactive state | 13. SPF-13 Authenticate | 13. ETC-13 Malformed ComPacket Header – Regular Session |
| 14. UCT-14 Revert the Admin SP using SID, with Locking SP in Mfg state | 14. SPF-15 Random | 14. ETC-14 Exceed TPer Properties – Regular Session |
| 15. UCT-15 Revert Admin SP using Admin1, with Locking SP in Mfg state | 15. SPF-16 CommonName | 15. ETC-15 Exceed TPer Properties – Control Session |
| 16. UCT-16 Revert Admin SP using PSID, with Locking SP in Manufactured state | 16. SPF-17 DataStore Table | 16. ETC-16 Overlapping Locking Ranges |
| 17. SPF-18 Range Crossing Behavior | 17. ETC-17 Invalid Type | |
| 18. SPF-19 Block SID Authentication | 18. ETC-18 RevertSP – GlobalRange Locked | |
| 19. ETC-19 Activate / ATA Security Interaction | ||
| 20. ETC-20 StartSession on Inactive Locking SP | ||
| 21. ETC-21 StartSession with Incorrect HostChallenge | ||
| 22. ETC-22 Multiple Sessions | ||
| 23. ETC-23 Data RemovalMechanism – Set Unsupported Value |
TCG Opal Protocol Test:
接下來驗證其Opal Protocol test是否符合TCG規範(TCG Storage Architecture Core Specification, Version 2.01; TCG Storage OPAL Test Cases Specification, Version 1.00),利用Opal Protocol Test針對儲存裝置進行functional check,確認回傳值是否符合spec規範。TCG Opal Protocol Test測試項目如下:
| a. OPALv1: | b. OPALv2: |
| 1. A0: Identify Device | 1. AlignSet_DataStore |
| 2. A1: Trusted Send/Receive | 2. AlignSet_LBA |
| 3. A2: Protocol ID = 0 related | 3. AlignSet_MBR |
| 4. A3: Level 0 Discovery | 4. Authenticate |
| 5. A4: Synchronous Communication Ptc | 5. Protocol2 |
| 6. A5: ComPacket/Packet/SubPacket | 6. Random |
| 7. A7: Transaction | 7. Revert_Effect2 |
| 8. A8: Ending Session | 8. StackReset |
| 9. A9: Empty Atom | 9. TPerInfo_SSC |
| 10. A10: Properties | 10. TPerReset |
| 11. A11: Start/SyncSession | 11. VerifyGeometry |
| 12. A6: Method_invoke/response | 12. RevertSP_Pyrite1_0 (for Pyrite1.00 device only) |
| 13. A12_Get_Byte_GramChk | 13. DataRemoval |
| 14. A13_Set_Byte_GramChk | 14. StartSyncSession_SessionTO |
| 15. A14_Next_AdminSP_GramChk | c. TableInfo: |
| 16. A15_GetACL_AdminSP_GramChk | 1. C1: Level 0 Discovery contents |
| 17. A19_RevertSP_GramChk | 2. C2: Properties() contents |
| 18. D1_ACESet | 3. C3: Get() contents |
| 19. D2_AuthoritySet | 4. C3_Get_ObjTable_LockSP_All |
| 20. D3_C_PINSet | 5. C4: Next() contents |
| 21. D4_LockingSet_RangeStartLength | 6. C5: GetACL() contents |
| 22. D4_LockingSet_WriteLock | d. Features: |
| 23. D5: MBRControl.Set | 1. Additional_DS |
| 24. D6: MBR.Set | 2. PSID |
| 25. D7: DataStore.Set() | 3. SingleUser |
| 26. D8: K_AES_*.GenKey | 4. BlockSID |
| 27. D9: Activate | |
| 28. D10: Revert()/RevertSP | |
| 29. D10_RevertSP_Effect | |
| 30. D11: Power Cycle |
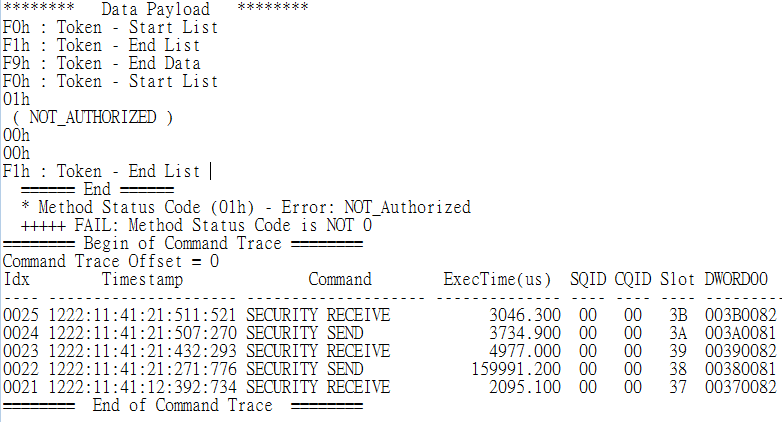
這邊舉一個實際案例與大家分享。符合TCG儲存裝置有個「shadow MBR」功能,使用者開啟此裝置時,會先進入一個稱為shadow MBR模擬空間進行pre-boot的身份驗證動作;通過驗證後,才會進入真正的開機程序,與裝置連結。在「UCT-10 Enable MBR Shadowing」這個item中,我們可以看到該裝置因在「subcase 2: Set on ACE_MBRControl_Set_DoneToDOR to include User1 and User8; Set Response: Pass」這個地方無法正常回傳對應值,無法取得認證,故此item便判定為Fail。
除了提供TCG Opal Certification Test & TCG Opal Protocol Test驗證報告以外,百佳泰也可以針對產品無法通過驗證的測項進行結果分析,協助廠商解決並通過驗證。相信透過這兩大項測試層層把關,通過嚴苛考驗的產品能在市面上帶給客戶信任感。